Data security with IIoT tools and practices
Jumping into the Industry 4.0 can be daunting. Then you start hearing things about data breaches, Blockchain, ransomware, Cambridge Analytica, hackers, and scandals. It’s important to ensure data is secure when you’re using cloud storage for your distributed system. Now, when IIoT is still quite new, security is one of the most often cited reasons people have for not adding IIoT features to their system. Here are a few things you can do to enhance data security and put minds at ease.
Integrated security and predictive approach
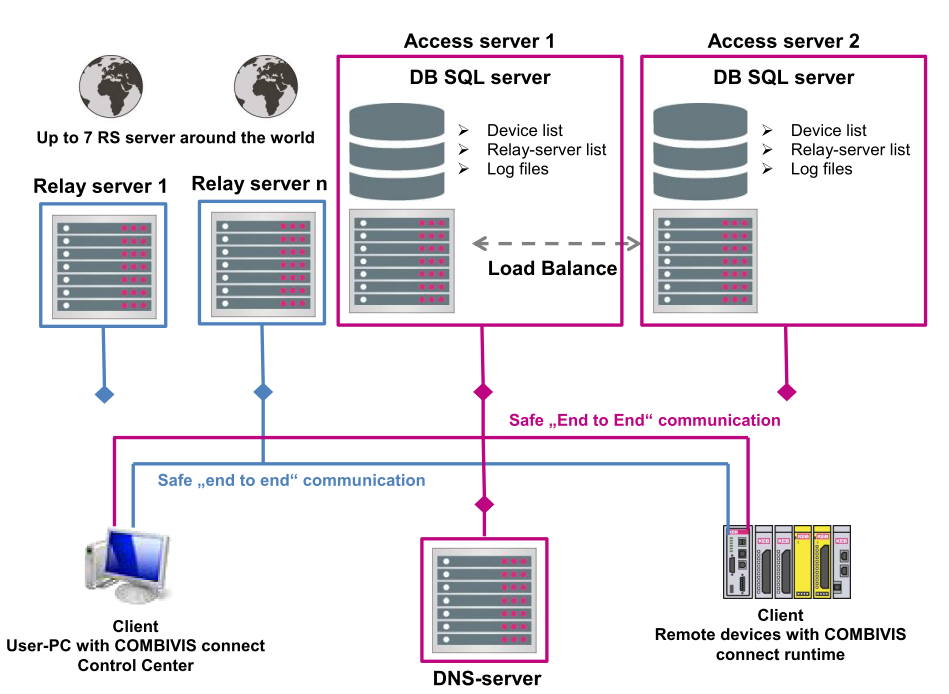
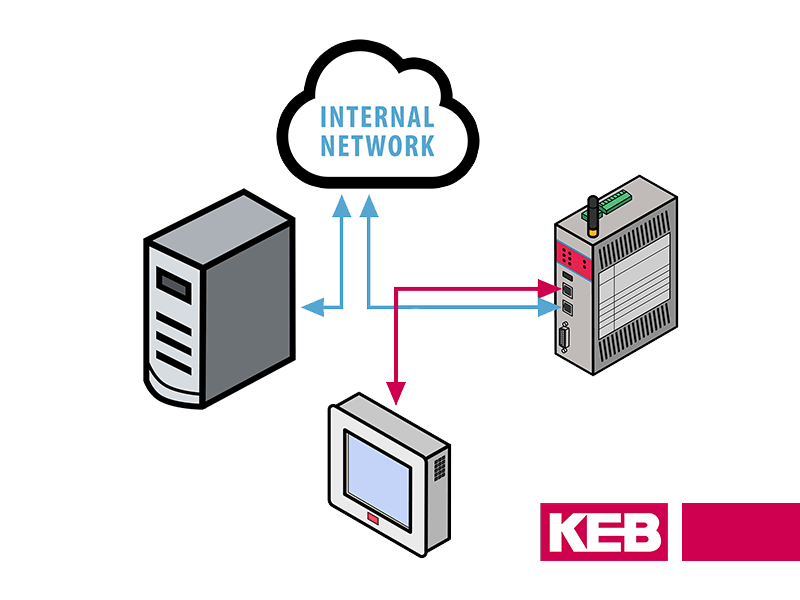
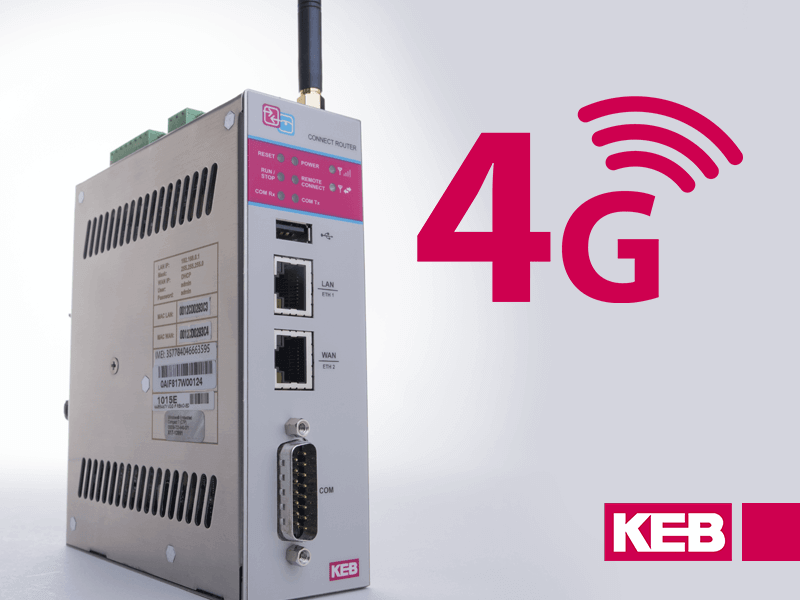
An integrator’s first steps to approaching security should be to consider integrated security and proactive, or predictive, measures. This includes ensuring firewalls are in place strong passwords are used where necessary. COMBIVIS Connect software from KEB America uses secure end-to-end VPN connections on a global server network. It allows administrators to create users with different levels of access, and can be used to create custom firewall properties. Finally, for even more peace-of-mind, it has been certified according to the industrial communication network security standards IEC 62443. This certification was awarded due to the successful audit carried out by the independent organization ProtectEM.
Some other preventative measures that are often suggested include having a breach plan or protocol available at all levels of management, so unauthorized access can be resolved with limited downtime.
Another suggestion sounds a bit like the exact opposite of what the Internet of Things is all about – and that’s to keep certain functions and operations isolated. Sharing data and analytics is great, and secure remote control and maintenance is a huge cost and time saving measure. But all benefits are for naught if it’s at the cost of trade secrets being snatched up, or entire systems being spontaneously taken down in one keystroke. If these functions are kept apart from the bulk of the data and communication being passed between machines, it is less likely to be vulnerable.
Analysis and reactive approach
When IoT is used in an industrial setting for control and automation, gathering data for analysis huge. Do not allow this data to simply gather dust in a folder somewhere. Review it in a timely manner, and take note of any possible attempts to access the system that are unauthorized. For any third-party software or devices you will also need to be on the lookout for patches and bug-fixes and apply them as quickly as possible. You may need to manage your customers’ expectations and let them know that some occasional downtime for system updates is necessary, and certainly preferable to downtime due to a security hack. Last year, the WannaCry virus devastated many systems simply because they were out-of-date. Had the latest security patches been applied, the ransomware would not have been as successful.
When building a networked system it’s important to remember that any breach in security will result in downtime. For an application to run with reliability security must be a consideration. If questions about security is preventing you or your client from using IIoT for faster and more reliable production, send us a message. Our engineers would be happy to help you find the right security solutions for your application.
Let's Work Together
Connect with us today to learn more about our industrial automation solutions—and how to commission them for your application.